核心思想
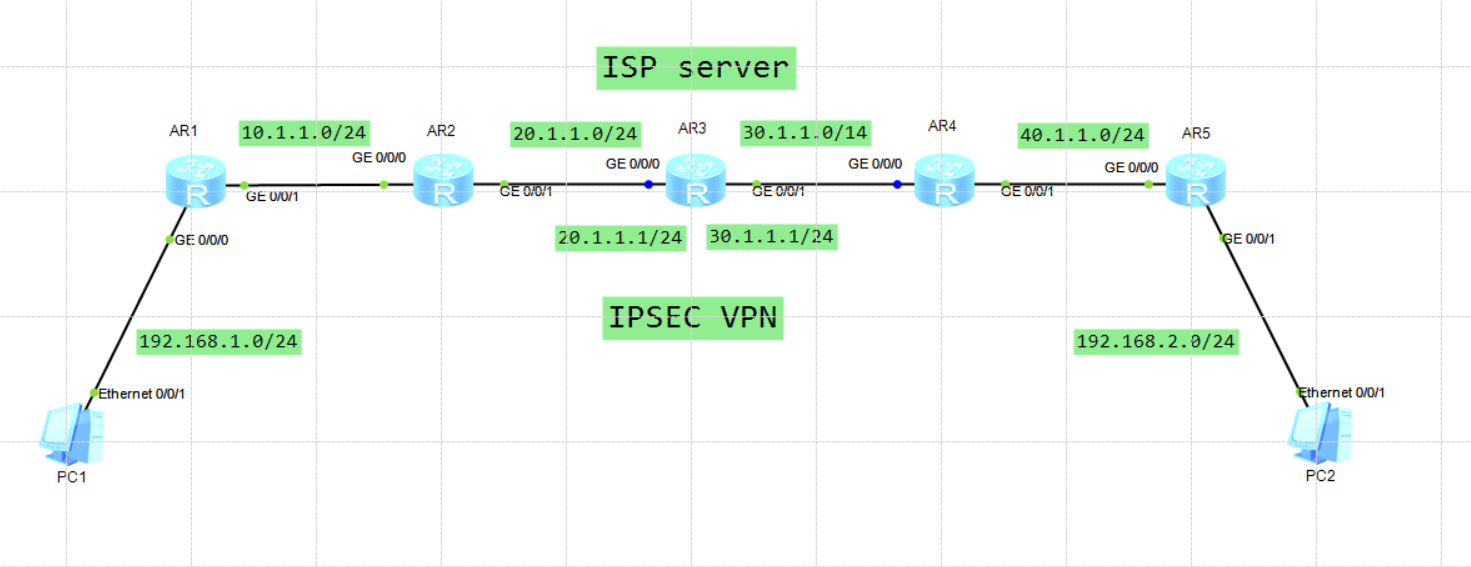
1)基础配置
每个接口配置IP地址
2)内部网络配置
ospf 100 router-id X.X.X.X
3)配置静态默认路由
ip route-static 0.0.0.0 0 出接口 下一跳
4)配置ipsec 协商 名称
ipsec proposal 2to4
5)配置感应兴趣流
acl number 3000
rule 5 permit ip source 网段 反掩码 destination 网段 反掩码
6)建立ipsec policy
ipsec policy yeslab 10 manual//策略名称
security acl 3000 //感兴趣安全数据流
proposal 2to4 //建议名称 2to4
tunnel local 20.1.1.2 //本地公网ip地址
tunnel remote 30.1.1.2 //对端公网ip地址g//
sa spi inbound esp 12345 //安全联盟协商参数
sa string-key inbound esp cipher %$%$}H"z!S,^u*;l(AQmOU4+,.2n%$%$
sa spi outbound esp 54321//安全联盟协商参数
sa string-key outbound esp cipher %$%$}H"z!S,^u*;l(AQmOU4+,.2n%$%$
7)安全策略在物理口应用
int g0/0/0
ipsec policy yeslab //调用安全策略名称
8)特别注意路由
需要将对端网段引入
ip route-static 对端目的网段 子网掩码 出接口 下一跳
详细配置内容
R1:
<r1>display current-configuration
[V200R003C00]
#
sysname r1
#
snmp-agent local-engineid 800007DB03000000000000
snmp-agent
#
clock timezone China-Standard-Time minus 08:00:00
#
portal local-server load portalpage.zip
#
drop illegal-mac alarm
#
set cpu-usage threshold 80 restore 75
#
aaa
authentication-scheme default
authorization-scheme default
accounting-scheme default
domain default
domain default_admin
local-user admin password cipher %$%$K8m.Nt84DZ}e#<0`8bmE3Uw}%$%$
local-user admin service-type http
#
firewall zone Local
priority 15
#
interface GigabitEthernet0/0/0
ip address 192.168.1.1 255.255.255.0
#
interface GigabitEthernet0/0/1
ip address 10.1.1.2 255.255.255.0
#
interface GigabitEthernet0/0/2
#
interface NULL0
#
interface LoopBack0
ip address 1.1.1.1 255.255.255.255
#
ospf 100 router-id 1.1.1.1
import-route static
area 0.0.0.0
network 10.1.1.0 0.0.0.255
network 192.168.1.0 0.0.0.255
#
ip route-static 192.168.2.0 255.255.255.0 GigabitEthernet0/0/1 10.1.1.1
#
user-interface con 0
authentication-mode password
user-interface vty 0 4
user-interface vty 16 20
#
wlan ac
#
return
<r1>
R2:
<r2>display current-configuration
[V200R003C00]
#
sysname r2
#
snmp-agent local-engineid 800007DB03000000000000
snmp-agent
#
clock timezone China-Standard-Time minus 08:00:00
#
portal local-server load portalpage.zip
#
drop illegal-mac alarm
#
set cpu-usage threshold 80 restore 75
#
acl number 3000
rule 5 permit ip source 192.168.1.0 0.0.0.255 destination 192.168.2.0 0.0.0.255
#
ipsec proposal 2to4
#
ipsec policy yeslab 10 manual
security acl 3000
proposal 2to4
tunnel local 20.1.1.2
tunnel remote 30.1.1.2
sa spi inbound esp 12345
sa string-key inbound esp cipher %$%$}H"z!S,^u*;l(AQmOU4+,.2n%$%$
sa spi outbound esp 54321
sa string-key outbound esp cipher %$%$}H"z!S,^u*;l(AQmOU4+,.2n%$%$
#
aaa
authentication-scheme default
authorization-scheme default
accounting-scheme default
domain default
domain default_admin
local-user admin password cipher %$%$K8m.Nt84DZ}e#<0`8bmE3Uw}%$%$
local-user admin service-type http
#
firewall zone Local
priority 15
#
interface GigabitEthernet0/0/0
ip address 10.1.1.1 255.255.255.0
#
interface GigabitEthernet0/0/1
ip address 20.1.1.2 255.255.255.0
ipsec policy yeslab
#
interface GigabitEthernet0/0/2
#
interface NULL0
#
interface LoopBack0
ip address 2.2.2.2 255.255.255.255
#
ospf 100 router-id 2.2.2.2
import-route direct
import-route static
area 0.0.0.0
network 10.1.1.0 0.0.0.255
#
ip route-static 0.0.0.0 0.0.0.0 GigabitEthernet0/0/1 20.1.1.1
ip route-static 192.168.1.0 255.255.255.0 GigabitEthernet0/0/0 10.1.1.2
#
user-interface con 0
authentication-mode password
user-interface vty 0 4
user-interface vty 16 20
#
wlan ac
#
return
<r2>
R3:
<r3>display current-configuration
[V200R003C00]
#
sysname r3
#
snmp-agent local-engineid 800007DB03000000000000
snmp-agent
#
clock timezone China-Standard-Time minus 08:00:00
#
portal local-server load portalpage.zip
#
drop illegal-mac alarm
#
set cpu-usage threshold 80 restore 75
#
aaa
authentication-scheme default
authorization-scheme default
accounting-scheme default
domain default
domain default_admin
local-user admin password cipher %$%$K8m.Nt84DZ}e#<0`8bmE3Uw}%$%$
local-user admin service-type http
#
firewall zone Local
priority 15
#
interface GigabitEthernet0/0/0
ip address 20.1.1.1 255.255.255.0
#
interface GigabitEthernet0/0/1
ip address 30.1.1.1 255.255.255.0
#
interface GigabitEthernet0/0/2
#
interface NULL0
#
user-interface con 0
authentication-mode password
user-interface vty 0 4
user-interface vty 16 20
#
wlan ac
#
return
<r3>
R4:
<r4>display current-configuration
[V200R003C00]
#
sysname r4
#
snmp-agent local-engineid 800007DB03000000000000
snmp-agent
#
clock timezone China-Standard-Time minus 08:00:00
#
portal local-server load portalpage.zip
#
drop illegal-mac alarm
#
set cpu-usage threshold 80 restore 75
#
acl number 3000
rule 5 permit ip source 192.168.2.0 0.0.0.255 destination 192.168.1.0 0.0.0.255
#
ipsec proposal 2to4
#
ipsec policy yeslab 10 manual
security acl 3000
proposal 2to4
tunnel local 30.1.1.2
tunnel remote 20.1.1.2
sa spi inbound esp 54321
sa string-key inbound esp cipher %$%$}H"z!S,^u*;l(AQmOU4+,.2n%$%$
sa spi outbound esp 12345
sa string-key outbound esp cipher %$%$}H"z!S,^u*;l(AQmOU4+,.2n%$%$
#
aaa
authentication-scheme default
authorization-scheme default
accounting-scheme default
domain default
domain default_admin
local-user admin password cipher %$%$K8m.Nt84DZ}e#<0`8bmE3Uw}%$%$
local-user admin service-type http
#
firewall zone Local
priority 15
#
interface GigabitEthernet0/0/0
ip address 30.1.1.2 255.255.255.0
ipsec policy yeslab
#
interface GigabitEthernet0/0/1
ip address 40.1.1.1 255.255.255.0
#
interface GigabitEthernet0/0/2
#
interface NULL0
#
interface LoopBack0
ip address 4.4.4.4 255.255.255.255
#
ospf 100 router-id 4.4.4.4
import-route direct
import-route static
area 0.0.0.0
network 40.1.1.0 0.0.0.255
#
ip route-static 0.0.0.0 0.0.0.0 GigabitEthernet0/0/0 30.1.1.1
ip route-static 192.168.2.0 255.255.255.0 GigabitEthernet0/0/1 40.1.1.2
#
user-interface con 0
authentication-mode password
user-interface vty 0 4
user-interface vty 16 20
#
wlan ac
#
return
<r4>
R5:
<r5>display current-configuration
[V200R003C00]
#
sysname r5
#
snmp-agent local-engineid 800007DB03000000000000
snmp-agent
#
clock timezone China-Standard-Time minus 08:00:00
#
portal local-server load portalpage.zip
#
drop illegal-mac alarm
#
set cpu-usage threshold 80 restore 75
#
aaa
authentication-scheme default
authorization-scheme default
accounting-scheme default
domain default
domain default_admin
local-user admin password cipher %$%$K8m.Nt84DZ}e#<0`8bmE3Uw}%$%$
local-user admin service-type http
#
firewall zone Local
priority 15
#
interface GigabitEthernet0/0/0
ip address 40.1.1.2 255.255.255.0
#
interface GigabitEthernet0/0/1
ip address 192.168.2.1 255.255.255.0
#
interface GigabitEthernet0/0/2
#
interface NULL0
#
interface LoopBack0
ip address 5.5.5.5 255.255.255.255
#
ospf 100 router-id 5.5.5.5
import-route static
area 0.0.0.0
network 40.1.1.0 0.0.0.255
network 192.168.2.0 0.0.0.255
#
ip route-static 192.168.1.0 255.255.255.0 GigabitEthernet0/0/0 40.1.1.1
#
user-interface con 0
authentication-mode password
user-interface vty 0 4
user-interface vty 16 20
#
wlan ac
#
return
<r5>
