知识点
1、network-entity 49.0001.0010.0100.1001.00
area id:49.0001
system id:0010.0100.1001
net:00
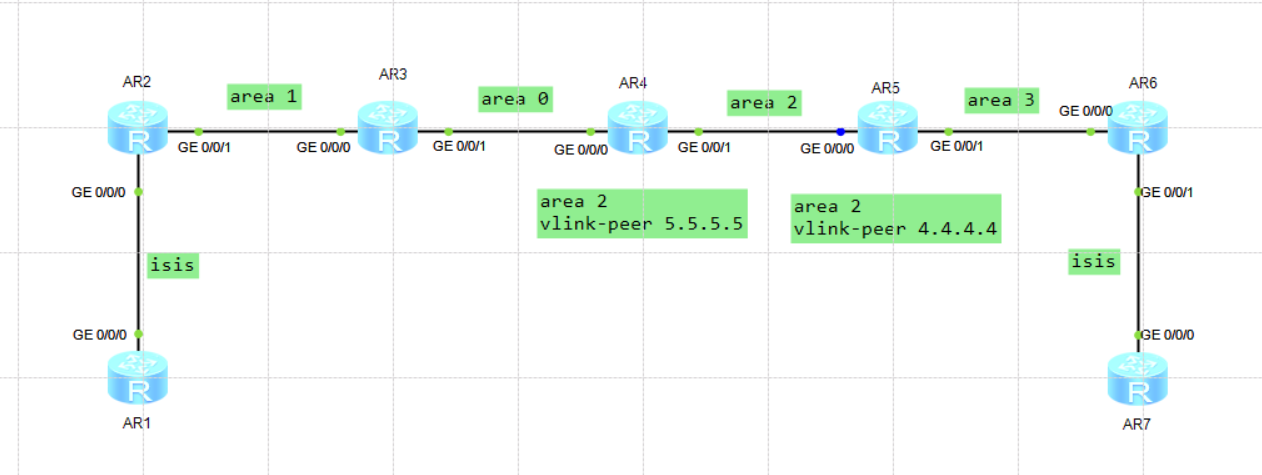
2、vlink-peer
area 1
vlink-peer 5.5.5.5
注意:本区域必须与骨干区域相连
3、ospf
ospf process //进程号
area id //区域号
network 宣告网段 通配符//通配符特点0需要严格匹配,1不需要匹配
配置
R1:
<r1>display current-configuration
[V200R003C00]
#
sysname r1
#
snmp-agent local-engineid 800007DB03000000000000
snmp-agent
#
clock timezone China-Standard-Time minus 08:00:00
#
portal local-server load portalpage.zip
#
drop illegal-mac alarm
#
set cpu-usage threshold 80 restore 75
#
aaa
authentication-scheme default
authorization-scheme default
accounting-scheme default
domain default
domain default_admin
local-user admin password cipher %$%$K8m.Nt84DZ}e#<0`8bmE3Uw}%$%$
local-user admin service-type http
#
isis 100
is-level level-2
cost-style wide
network-entity 49.0001.0010.0100.1001.00
#
firewall zone Local
priority 15
#
interface GigabitEthernet0/0/0
ip address 12.1.1.1 255.255.255.0
isis enable 100
#
interface GigabitEthernet0/0/1
#
interface GigabitEthernet0/0/2
#
interface NULL0
#
interface LoopBack0
ip address 1.1.1.1 255.255.255.255
isis enable 100
#
ospf 1
#
user-interface con 0
authentication-mode password
user-interface vty 0 4
user-interface vty 16 20
#
wlan ac
#
return
<r1>
R2:
<r2>display current-configuration
[V200R003C00]
#
sysname r2
#
snmp-agent local-engineid 800007DB03000000000000
snmp-agent
#
clock timezone China-Standard-Time minus 08:00:00
#
portal local-server load portalpage.zip
#
drop illegal-mac alarm
#
set cpu-usage threshold 80 restore 75
#
aaa
authentication-scheme default
authorization-scheme default
accounting-scheme default
domain default
domain default_admin
local-user admin password cipher %$%$K8m.Nt84DZ}e#<0`8bmE3Uw}%$%$
local-user admin service-type http
#
isis 100
is-level level-2
cost-style wide
network-entity 49.0001.0020.0200.2002.00
import-route ospf 200
#
firewall zone Local
priority 15
#
interface GigabitEthernet0/0/0
ip address 12.1.1.2 255.255.255.0
isis enable 100
#
interface GigabitEthernet0/0/1
ip address 23.1.1.2 255.255.255.0
ospf enable 200 area 0.0.0.1
#
interface GigabitEthernet0/0/2
#
interface NULL0
#
interface LoopBack0
ip address 2.2.2.2 255.255.255.255
ospf enable 200 area 0.0.0.1
#
ospf 200 router-id 2.2.2.2
import-route isis 100
area 0.0.0.1
#
user-interface con 0
authentication-mode password
user-interface vty 0 4
user-interface vty 16 20
#
wlan ac
#
return
<r2>
R3:
<r3>display current-configuration
[V200R003C00]
#
sysname r3
#
snmp-agent local-engineid 800007DB03000000000000
snmp-agent
#
clock timezone China-Standard-Time minus 08:00:00
#
portal local-server load portalpage.zip
#
drop illegal-mac alarm
#
set cpu-usage threshold 80 restore 75
#
aaa
authentication-scheme default
authorization-scheme default
accounting-scheme default
domain default
domain default_admin
local-user admin password cipher %$%$K8m.Nt84DZ}e#<0`8bmE3Uw}%$%$
local-user admin service-type http
#
firewall zone Local
priority 15
#
interface GigabitEthernet0/0/0
ip address 23.1.1.3 255.255.255.0
#
interface GigabitEthernet0/0/1
ip address 34.1.1.3 255.255.255.0
#
interface GigabitEthernet0/0/2
#
interface NULL0
#
interface LoopBack0
ip address 3.3.3.3 255.255.255.255
#
ospf 200 router-id 3.3.3.3
area 0.0.0.0
network 34.1.1.0 0.0.0.255
area 0.0.0.1
network 3.3.3.3 0.0.0.0
network 23.1.1.0 0.0.0.255
#
user-interface con 0
authentication-mode password
user-interface vty 0 4
user-interface vty 16 20
#
wlan ac
#
return
<r3>
R4:
<r4>display current-configuration
[V200R003C00]
#
sysname r4
#
snmp-agent local-engineid 800007DB03000000000000
snmp-agent
#
clock timezone China-Standard-Time minus 08:00:00
#
portal local-server load portalpage.zip
#
drop illegal-mac alarm
#
set cpu-usage threshold 80 restore 75
#
aaa
authentication-scheme default
authorization-scheme default
accounting-scheme default
domain default
domain default_admin
local-user admin password cipher %$%$K8m.Nt84DZ}e#<0`8bmE3Uw}%$%$
local-user admin service-type http
#
firewall zone Local
priority 15
#
interface GigabitEthernet0/0/0
ip address 34.1.1.4 255.255.255.0
#
interface GigabitEthernet0/0/1
ip address 45.1.1.4 255.255.255.0
#
interface GigabitEthernet0/0/2
#
interface NULL0
#
interface LoopBack0
ip address 4.4.4.4 255.255.255.255
#
ospf 200 router-id 4.4.4.4
area 0.0.0.0
network 4.4.4.4 0.0.0.0
network 34.1.1.0 0.0.0.255
area 0.0.0.2
network 45.1.1.0 0.0.0.255
vlink-peer 5.5.5.5
#
user-interface con 0
authentication-mode password
user-interface vty 0 4
user-interface vty 16 20
#
wlan ac
#
return
<r4>
R5:
<r5>display current-configuration
[V200R003C00]
#
sysname r5
#
snmp-agent local-engineid 800007DB03000000000000
snmp-agent
#
clock timezone China-Standard-Time minus 08:00:00
#
portal local-server load portalpage.zip
#
drop illegal-mac alarm
#
set cpu-usage threshold 80 restore 75
#
aaa
authentication-scheme default
authorization-scheme default
accounting-scheme default
domain default
domain default_admin
local-user admin password cipher %$%$K8m.Nt84DZ}e#<0`8bmE3Uw}%$%$
local-user admin service-type http
#
firewall zone Local
priority 15
#
interface GigabitEthernet0/0/0
ip address 45.1.1.5 255.255.255.0
#
interface GigabitEthernet0/0/1
ip address 56.1.1.5 255.255.255.0
#
interface GigabitEthernet0/0/2
#
interface NULL0
#
interface LoopBack0
ip address 5.5.5.5 255.255.255.255
#
ospf 200 router-id 5.5.5.5
area 0.0.0.2
network 5.5.5.5 0.0.0.0
network 45.1.1.0 0.0.0.255
vlink-peer 4.4.4.4
area 0.0.0.3
network 56.1.1.0 0.0.0.255
#
user-interface con 0
authentication-mode password
user-interface vty 0 4
user-interface vty 16 20
#
wlan ac
#
return
<r5>
R6:
<r6>display current-configuration
[V200R003C00]
#
sysname r6
#
snmp-agent local-engineid 800007DB03000000000000
snmp-agent
#
clock timezone China-Standard-Time minus 08:00:00
#
portal local-server load portalpage.zip
#
drop illegal-mac alarm
#
set cpu-usage threshold 80 restore 75
#
aaa
authentication-scheme default
authorization-scheme default
accounting-scheme default
domain default
domain default_admin
local-user admin password cipher %$%$K8m.Nt84DZ}e#<0`8bmE3Uw}%$%$
local-user admin service-type http
#
isis 100
is-level level-2
cost-style wide
network-entity 49.0002.0060.0600.6006.00
import-route ospf 200
#
firewall zone Local
priority 15
#
interface GigabitEthernet0/0/0
ip address 56.1.1.6 255.255.255.0
#
interface GigabitEthernet0/0/1
ip address 67.1.1.6 255.255.255.0
isis enable 100
#
interface GigabitEthernet0/0/2
#
interface NULL0
#
interface LoopBack0
ip address 6.6.6.6 255.255.255.255
#
ospf 200 router-id 6.6.6.6
import-route isis 100
area 0.0.0.3
network 6.6.6.6 0.0.0.0
network 56.1.1.0 0.0.0.255
#
user-interface con 0
authentication-mode password
user-interface vty 0 4
user-interface vty 16 20
#
wlan ac
#
return
<r6>
R7:
<r7>display current-configuration
[V200R003C00]
#
sysname r7
#
snmp-agent local-engineid 800007DB03000000000000
snmp-agent
#
clock timezone China-Standard-Time minus 08:00:00
#
portal local-server load portalpage.zip
#
drop illegal-mac alarm
#
set cpu-usage threshold 80 restore 75
#
aaa
authentication-scheme default
authorization-scheme default
accounting-scheme default
domain default
domain default_admin
local-user admin password cipher %$%$K8m.Nt84DZ}e#<0`8bmE3Uw}%$%$
local-user admin service-type http
#
isis 100
is-level level-2
cost-style wide
network-entity 49.0002.0070.0700.7007.00
#
firewall zone Local
priority 15
#
interface GigabitEthernet0/0/0
ip address 67.1.1.7 255.255.255.0
isis enable 100
#
interface GigabitEthernet0/0/1
#
interface GigabitEthernet0/0/2
#
interface NULL0
#
interface LoopBack0
ip address 7.7.7.7 255.255.255.255
isis enable 100
#
user-interface con 0
authentication-mode password
user-interface vty 0 4
user-interface vty 16 20
#
wlan ac
#
return
<r7>
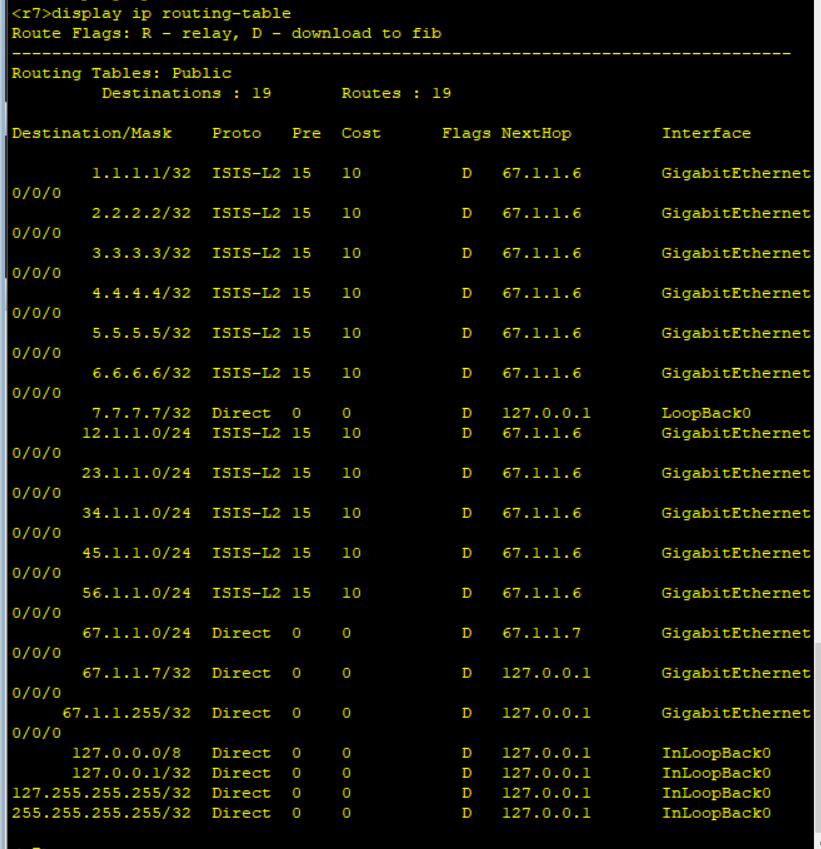
输出结果